Articles Archive
16 Dec 2018
Investing in Hacking

It’s said that many investors have moved their fortunes from gold to bitcoin and other crypto currencies. Investing in crypto currencies comes with a big risc and we would like to look for alternative segments which also have growth. Security stocks is globally in a growing trend at the stock market and this is something that
31 Aug 2015
Buffer Overflow Attacks
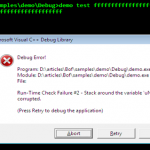
In an era where everything is digitized, there is always some scope for a loophole or vulnerability. This loophole forms the crux where hackers squeeze in their mischievous codes and hence flourish their business. You may expect a businessman to cut loose his profit, but you can never bargain on an attacker to miss vulnerability
15 May 2015
Best practices for cloud services
Introduction Today most people have a smart phone, tablet or PC. Some years back we stored our photos on backup media such as CD or DVDs. Today different companies compete about getting access to our files. Most people today doesn’t react when a new “app” is installed and permissions is asked to our pictures, private messages or
27 Apr 2015
Cloaking WordPress with “hide my WP”?

There’s a bunch of companies that provides services for cloaking the user’s website. In the previous articles Web scraping – part 1 and Web scraping – part 2 we learned how easy it was to scan multiple sites for vulnerabilities using footprints. This very exact method is dependent on that out footprints can be found on the site –
08 Apr 2015
Net phishing
In this post I’m going to discuss about net phishing (also referred to as “web spoofing”). I still hear about people that have lost real money because of net phishing – and that´s just sad. Net phishing isn’t a new technique and neither a qualified hacking technique, but then keep in mind that most hacks today is based on old hacks,
11 Mar 2015
Web scraping – part 2
Web scraping In the previous article we identified the footprints to use and now it’s time to start coding. First we need to fetch content from a website. In PHP we can do this using CURL or file_get_contents. Downloading source code from website You’ll need a text editor. For this project I picked sublime. To
27 Feb 2015
Web scraping – part 1
Web scraping When a hacker has identified a vulnerability in a system or platform he can choose to either report it (white hat hacker) or scan more systems with the same security hole. One way to do this is “Web scraping” which means scanning a website for specific areas and/or extracting that information. Web scraping
18 Feb 2015
Protected: Trick to access to thousands of premium products.
There is no excerpt because this is a protected post.
08 Nov 2014
Review of jSpy a RAT from jSpy.net
Review of jSpy Current version: 0.33 Developer URL: http://www.jspy.net/jspy/ Remote administrating tools with features such as webcam capture is nothing else then what earlier was named as trojans. We decided to check out jSpy just because the developer states that no buyers must write anything bad about it in public. Features Features jSpy 100%
20 Aug 2014
Bypassing windows login screen – with Kon-Boot
System Requirements: Kon-Boot 1.0 works with the 32-bit Windows versions including XP, Vista and a few Windows Server OS’s. Kon-boot is just one of many great tools out on the Internet. It has the power to remove all passwords by temporary modifying BIOS. Unfortunately it seems like the free version recently got removed from
- 1
- 2